The Unified Kill Chain: Your Tool for Actively Evaluating Your Cyber Defenses
April/May Month in Review
Presented by Jeff Garrett, Opkalla VP of Solutions Architecture
As promised, we are rolling right along into our next topic. This time it’s all about cybersecurity.
A Challenge: Guiding Customers Through the Ever-Changing Cybersecurity Landscape
Over the last year at Opkalla we have been in search of better ways to address the ever-changing cybersecurity landscape with our customers.
We all know there is no silver bullet when it comes to cybersecurity. Layers of process, procedure and tools are needed to help cover gaps in an organization’s environment.
While comprehensive frameworks like NIST and CIS provide valuable long-term strategies, businesses often seek quick reference guides to assess their security posture in a fast and efficient manner. Questions like “Is there anything we are missing?” or “What are the latest trends?” often come up in conversation. But without a guide, it is extremely tough to make sure we are consistently asking these questions across all areas of the cybersecurity landscape.
Our Solution: The Kill Chain Approach
As we considered different approaches, we ultimately landed on using a kill chain approach to guide the conversation. There are many variations of cybersecurity kill chains in use today. We needed something that was not too high level nor too in the weeds. We're talking something that could fit into a two-hour conversation and help our customers quickly gauge where in their environment they need to take a closer look.
For us, that guide has become The Unified Kill Chain. Over the last month we have been using this heavily to help customers take a high-level look at their environments. From there, we quickly set their focus on critical areas or gaps in their solutions and procedures.
Below I’ll dive into:
What exactly The Unified Kill Chain is
The three phases included in the model
How we are using Unified Kill Chain to strengthen our customers’ cybersecurity awareness and overall posture
The Unified Kill Chain: What It Is
The Unified Kill Chain incorporates key elements from two renowned cybersecurity frameworks:
The Lockheed Martin Kill Chain
The MITRE ATT&CK Framework
By leveraging the strengths of these frameworks, the Unified Kill Chain provides organizations with a comprehensive evaluation tool.
The Lockheed Martin Kill Chain offers a systematic view of an attacker's intrusion stages, while the MITRE ATT&CK Framework provides a detailed catalog of adversary tactics and techniques. Through the integration of these frameworks, the Unified Kill Chain enables organizations to assess their defenses from both (1) a strategic perspective, considering attack phases, and (2) a tactical standpoint, focusing on specific adversary behaviors.
This combination empowers organizations to gain a holistic understanding of their security posture and align their defensive measures accordingly. The result? A stronger, more effective cybersecurity strategy.
The Three Main Phases of the Unified Kill Chain Model
The Unified Kill Chain offers a simplified yet comprehensive view of an attacker's journey using a breakdown of three main phases. Each phase contains threat actor high-level actions to consider. Below we will take a brief look at each.
Phase 1: Initial Foothold
The Initial Foothold phase involves an attacker gaining access to an organization's network. It includes eight sub phases or actions that need to be considered:
Reconnaissance
Weaponization
Delivery
Social Engineering
Exploitation
Persistence
Defense Evasion
Command & Control
Key defensive areas to help break the chain in this phase revolve around users. These include:
Email security
Endpoint security
Multi-factor authentication
User awareness training and testing
These are all key in preventing a threat actor from gaining initial access and establishing a foothold.
A few other key defensive areas here that do not pertain entirely to the end user are:
Properly configured network firewalls
Vulnerability scanning
Comprehensive patching
Phase 2: Network Propagation
During the Network Propagation phase, attackers aim to spread within the organization's network and escalate privileges. This phase includes six sub phases or actions that need to be considered across ALL systems, code and clouds on the network. These include:
Pivoting
Discovery
Privilege Escalation
Execution
Credential Access
Lateral Movement
Key areas to consider here cover overall networking security, which includes:
Firewalls
Network monitoring and VPN control
Identity and Access Management controls
Other growing areas of concern (brought to light with some recent well-known attacks) are:
Infrastructure security (OT/ICS and IoT)
Application security (specifically code security)
Cloud security (misconfigured resources)
These are increasingly vulnerable areas that threat actors want to exploit to (1) not only get wider in a single organization’s environment, but (2) to also potentially gain access and impact their customers.
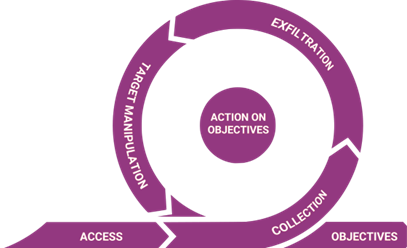
Phase 3: Action on Objectives
The Action on Objectives phase involves attackers achieving their goals, such as data exfiltration or system manipulation. This phase only has a few sub phases or actions, but all deal with a direct impact on an organization’s systems and data:
Access
Collection
Exfiltration
Target Manipulation
Objectives
Some traditional considerations to help within this phase are:
Data backups
Disaster recovery planning
Overall incident response planning.
Security operations also plays a major part in this phase as these teams, whether in-house or as-a-service, are now the first responders to the attacks against systems and data.
One final key area to consider here is data security and data loss prevention. So many of today’s attacks not only aim to encrypt data, but also to exfiltrate data from your environment.
How We Are Strengthening Our Customers’ Cybersecurity Awareness and Overall Posture with Unified Kill Chain
Leveraging the Unified Kill Chain's three main phases provides organizations with numerous security benefits:
Targeted Enhancements: By identifying gaps within each phase of the kill chain, businesses can focus on implementing specific enhancements and controls tailored to their vulnerabilities. This ensures a more effective defense strategy.
Risk Mitigation: Assessing security solutions against the Unified Kill Chain enables organizations to prioritize and allocate resources to address high-risk areas. This reduces the potential impact of cyber threats.
Continuous Improvement: Regularly reassessing defenses using the Unified Kill Chain fosters a culture of continuous improvement. Organizations can adapt to emerging threats and proactively enhance their cybersecurity posture.
Informed Decision-Making: Understanding security gaps enables organizations to make informed decisions when investing in new technologies, implementing additional controls, or adjusting existing security practices.
Actively Evaluate Your Cyber Defenses with Unified Kill Chain
As the cyber threat landscape continues to evolve, businesses must actively evaluate their cybersecurity defenses. The Unified Kill Chain, focusing on the three main phases of Initial Foothold, Network Propagation, and Action on Objectives, offers a simplified approach to assess security postures and uncover potential vulnerabilities. By leveraging this framework, organizations can strengthen their defenses, mitigate risks, and maintain a robust security posture in the face of evolving threats.
To learn more about The Unified Kill Chain, send us a message and we’ll set up your own Kill Chain Review session. Visit the Unified Kill Chain main site at https://www.unifiedkillchain.com/ for immediate extra info.